[kc_row _id="592709"][kc_column width="12/12" video_mute="no" _id="749855"][experience-block _id="888608" heading="Addressing Popular IT Security Myths" experience_list="eyIxIjp7InBvc2l0aW9uIjoiQWRkcmVzc2luZyBQb3B1bGFyIElUIFNlY3VyaXR5IE15dGhzIiwiY29tcGFueSI6IiBAIEVza2lsbHMgQWNhZGVteSIsInN0YXJ0X2RhdGUiOiIyMDIxIiwic3RhcnRlbmRfc2VwYXJhdG9yIjoiIiwiY3VycmVudCI6InllcyIsImN1cnJlbnRfdGV4dCI6IiAtIEFkZHJlc3NpbmcgUG9wdWxhciBJVCBTZWN1cml0eSBNeXRocyAtIEZvcm1hdGlvbiBkZSAxSCIsImVuZF9kYXRlIjoiIiwiZGVzY3JpcHRpb24iOiJQSFZzUGcwS1BHeHBJR2xrUFNKc1pXTjBkWEpsWDJobFlXUnBibWNpSUdOc1lYTnpQU0p6WldOMGFXOXVMWFJwZEd4bElHUnpjQzFtYkdWNExYaHpJR1pzWlhndFlXeHBaMjR0YVhSbGJYTXRZMlZ1ZEdWeUxYaHpJaUJrWVhSaExXeGxZM1IxY21VdGFXUTlJakUwTVRZM01EWTVJaUJrWVhSaExXNWxlSFF0YkdWamRIVnlaUzFwWkQwaU1UUXhOamN3TmpnaUlHUmhkR0V0YkdWamRIVnlaUzExY213OUlpOWpiM1Z5YzJWekx6YzRNRFU0T0M5c1pXTjBkWEpsY3k4eE5ERTJOekEyT1NJZ1pHRjBZUzF1WlhoMExXeGxZM1IxY21VdGRYSnNQU0l2WTI5MWNuTmxjeTgzT0RBMU9EZ3ZiR1ZqZEhWeVpYTXZNVFF4Tmpjd05qZ2lQazl5YVdkcGJuTWdiMllnU1ZRZ1UyVmpkWEpwZEhrZ1RYbDBhSE04TDJ4cFBnMEtQR3hwSUdOc1lYTnpQU0p6WldOMGFXOXVMWFJwZEd4bElHUnpjQzFtYkdWNExYaHpJR1pzWlhndFlXeHBaMjR0YVhSbGJYTXRZMlZ1ZEdWeUxYaHpJaUJrWVhSaExXeGxZM1IxY21VdGFXUTlJakUwTVRZM01EWTVJaUJrWVhSaExXNWxlSFF0YkdWamRIVnlaUzFwWkQwaU1UUXhOamN3TmpnaUlHUmhkR0V0YkdWamRIVnlaUzExY213OUlpOWpiM1Z5YzJWekx6YzRNRFU0T0M5c1pXTjBkWEpsY3k4eE5ERTJOekEyT1NJZ1pHRjBZUzF1WlhoMExXeGxZM1IxY21VdGRYSnNQU0l2WTI5MWNuTmxjeTgzT0RBMU9EZ3ZiR1ZqZEhWeVpYTXZNVFF4Tmpjd05qZ2lQbGx2ZGVLQW1XeHNJRTVsZG1WeUlFSmxJRWhoWTJ0bFpEd3ZiR2srRFFvOGJHa2dZMnhoYzNNOUluTmxZM1JwYjI0dGRHbDBiR1VnWkhOd0xXWnNaWGd0ZUhNZ1pteGxlQzFoYkdsbmJpMXBkR1Z0Y3kxalpXNTBaWEl0ZUhNaUlHUmhkR0V0YkdWamRIVnlaUzFwWkQwaU1UUXhOamN3TmpraUlHUmhkR0V0Ym1WNGRDMXNaV04wZFhKbExXbGtQU0l4TkRFMk56QTJPQ0lnWkdGMFlTMXNaV04wZFhKbExYVnliRDBpTDJOdmRYSnpaWE12Tnpnd05UZzRMMnhsWTNSMWNtVnpMekUwTVRZM01EWTVJaUJrWVhSaExXNWxlSFF0YkdWamRIVnlaUzExY213OUlpOWpiM1Z5YzJWekx6YzRNRFU0T0M5c1pXTjBkWEpsY3k4eE5ERTJOekEyT0NJK1ZHOTBZV3dnUTI5dGNIVjBaWElnVTJWamRYSnBkSGtnYVhNZ1VISnBiM0pwZEhrOEwyeHBQZzBLUEd4cElHTnNZWE56UFNKelpXTjBhVzl1TFhScGRHeGxJR1J6Y0MxbWJHVjRMWGh6SUdac1pYZ3RZV3hwWjI0dGFYUmxiWE10WTJWdWRHVnlMWGh6SWlCa1lYUmhMV3hsWTNSMWNtVXRhV1E5SWpFME1UWTNNRFk1SWlCa1lYUmhMVzVsZUhRdGJHVmpkSFZ5WlMxcFpEMGlNVFF4Tmpjd05qZ2lJR1JoZEdFdGJHVmpkSFZ5WlMxMWNtdzlJaTlqYjNWeWMyVnpMemM0TURVNE9DOXNaV04wZFhKbGN5OHhOREUyTnpBMk9TSWdaR0YwWVMxdVpYaDBMV3hsWTNSMWNtVXRkWEpzUFNJdlkyOTFjbk5sY3k4M09EQTFPRGd2YkdWamRIVnlaWE12TVRReE5qY3dOamdpUGs1dklIQnliM1JsWTNScGIyNGdVMjltZEhkaGNtVWdiM0lnU0dGeVpIZGhjbVVnVW1WeGRXbHlaV1E4TDJ4cFBnMEtQQzkxYkQ0TkNnPT0ifX0="][skills-block _id="147640" skills_list="eyIxIjp7InNraWxsX3RpdGxlIjoiQWRkcmVzc2luZyBQb3B1bGFyIElUIFNlY3VyaXR5IE15dGhzIiwieWVhcnNfZXhwZXJpZW5jZSI6IiIsInNraWxsX3BlcmNlbnQiOiIxMDAlIn19"][/kc_column][/kc_row]
Read MoreBlog Category: CyberSecurity
CERTIFIED ETHICAL HACKING – MASTER COURSE 2021 – Addressing Popular IT Security Myths
22 novembre 2021 CyberSecurity, Ethical Hack, Hacking, Sécurité, Software Cybersecurity
CERTIFIED ETHICAL HACKING – MASTER COURSE 2021 – Introduction to Current Cyber Threats
22 novembre 2021 CyberSecurity, Ethical Hack, Informatique, NetWork, Sécurité Cybersecurity
Introduction to Current Cyber Threats Introduction to Current Cyber Threats @ Eskills Academy 2021 - Introduction to Current Cyber Threats - Formation de 1H IT Practices Prehistory Evolution of Cyber Crimes History of IT Vulnerability
Read MoreCERTIFIED ETHICAL HACKING – MASTER COURSE 2021 – Ethical Hacking Practices 2021: IT Surveillance and Computer Forensics
22 novembre 2021 CyberSecurity, Ethical Hack, Informatique, Linux, NetWork, Sécurité, Software Cybersecurity
Ethical Hacking Practices 2021: IT Surveillance and Computer Forensics Ethical Hacking Practices 2021: IT Surveillance and Computer Forensics @ Eskills Academy 2021 - Ethical Hacking Practices 2021: IT Surveillance and Computer Forensics - Formation de
Read MoreCERTIFIED ETHICAL HACKING – Master Course 2021 – Ethical Hacking Practices 2021: Complete Guide to Cyber Risk Management
22 novembre 2021 CyberSecurity, Informatique, NetWork, OS, Sécurité Cybersecurity
Ethical Hacking Practices 2021: Complete Guide to Cyber Risk Management Ethical Hacking Practices 2021: Complete Guide to Cyber Risk Management @ Eskills Academy 2021 - Ethical Hacking Practices 2021: Complete Guide to Cyber Risk Management
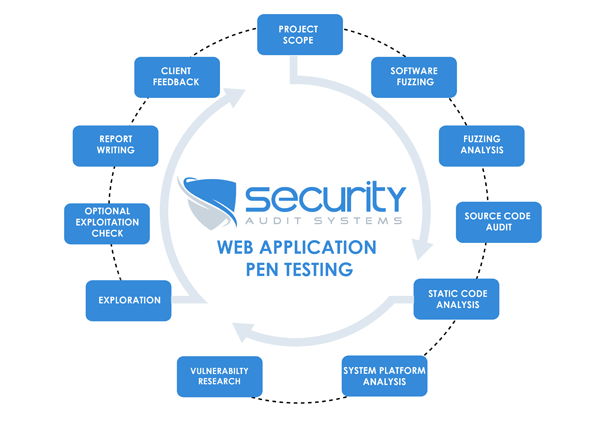
Read MoreLearn Ethical Hacking & Web Application Penetration Testing
18 novembre 2021 Administrateur réseaux, Android, CyberSecurity, Ethical Hack, Linux, NetWork, OS, Sécurité, WebDeveloper, Webmaster Cybersecurity
Learn Ethical Hacking & Web Application Penetration Testing Learn Ethical Hacking & Web Application Penetration Testing @ Udemy 2019 - Learn Ethical Hacking & Web Application Penetration Testing - Formation de 32H Course Introduction -
Read MoreThe Complete Cyber Security & Hacking Course
17 novembre 2021 CyberSecurity, Ethical Hack, Informatique, Linux, NetWork, Sécurité, WebDeveloper, Webmaster
The Complete Cyber Security & Hacking Course The Complete Cyber Security & Hacking Course @ EH Academy 02-2019 - The Complete Cyber Security & Hacking Course - Formation de 8H Computer Basics & Introduction Setting
Read MoreWordPress Security – Secure your site quickly and effectively
16 novembre 2021 CyberSecurity, Developer, Ethical Hack, Sécurité, WebDeveloper, Webmaster
WordPress Security - Secure your site quickly and effectively WordPress Security - Secure your site quickly and effectively @ EH Academy 01-2019 WordPress Security - Secure your site quickly and effectively - Formation de 6h
Read MoreCertification Linux LPIC-1/101 ou Comptia LX0-103
5 mai 2021 Administrateur réseaux, CyberSecurity, Informatique, Linux, NetWork, OS, Sécurité, System
CERTIFICATION LINUX LPIC-1/101 OU COMPTIA LX0-103 @ Udemy 2018- CERTIFICATION LINUX LPIC-1/101 OU COMPTIA LX0-103 - Formation de 8,5H Introduction Laboratoire gnu et unix commande Linux file system et hardware Architecture system Installation de package
Read MoreKali Linux Tutorial For Beginners
5 mai 2021 Administrateur réseaux, CyberSecurity, Ethical Hack, Linux, NetWork, Sécurité, System
Kali Linux Tutorial For Beginners @ Udemy 2018- Kali Linux Tutorial For Beginners - Formation de 8H Welcome! Before You Install Kali Installing Kali Building The Foundations Administration Hacking With Kali Linux Shells Used By
Read MoreLes Réseaux de A à Z | Passe l’examen Cisco ICND1 100-101
5 mai 2021 Administrateur réseaux, CyberSecurity, Informatique, NetWork
Les Réseaux de A à Z | Passe l'examen Cisco ICND1 100-101 @ Udemy 2019- Les Réseaux de A à Z | Passe l'examen Cisco ICND1 100-101 - Formation de 8H Présentation de la formation
Read More